Data Security Learning Module
Block Cipher Operation Modes
Created By Eng. Eslam Osama
Introduction to Block Cipher Modes
What are Block Cipher Operation Modes?
Block cipher operation modes are algorithms that define how block ciphers (like AES or DES) are applied to securely encrypt data larger than a single block. They provide different approaches to handle data encryption with unique security properties and performance characteristics.
Why are different modes needed?
-
To securely encrypt data larger than a single block size
-
To provide different security and performance trade-offs
-
To handle various application requirements (streaming data, parallel processing, etc.)
-
To prevent pattern recognition in encrypted data
Key Concepts
Block Cipher
A symmetric encryption algorithm that transforms a fixed-length block of plaintext into ciphertext
- Common block sizes: 64-bit (DES), 128-bit (AES)
- Requires modes to encrypt data larger than block size
Initialization Vector (IV)
A random starting value used in several modes to ensure different ciphertexts for same plaintext
- Must be unpredictable and unique
- Typically not secret, but must be stored/transmitted securely
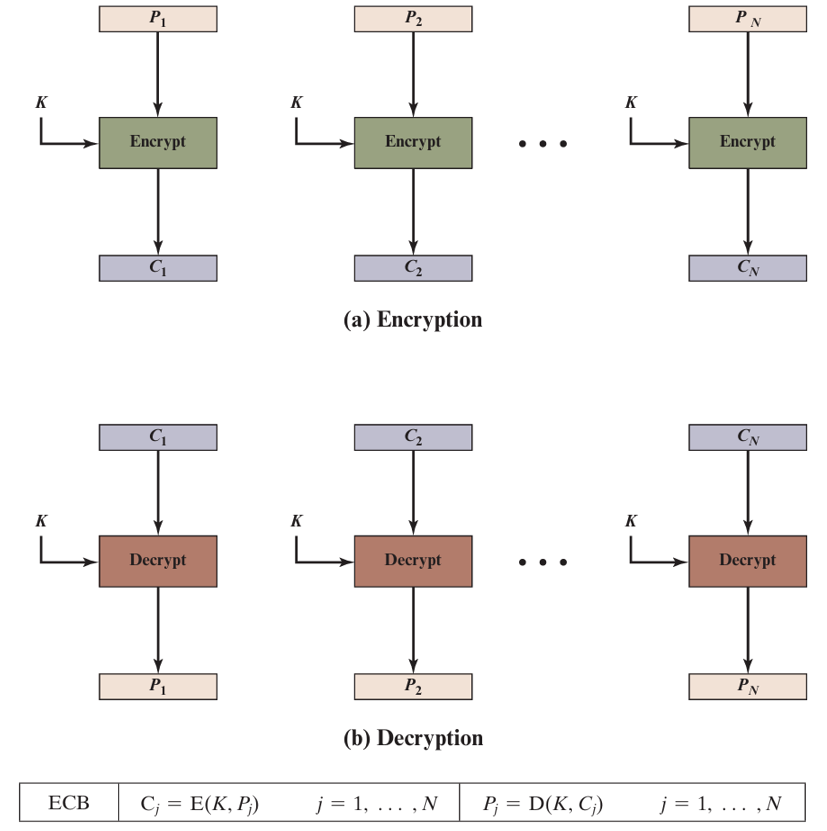
Electronic Codebook (ECB) Mode
Electronic Codebook (ECB) Mode
The simplest encryption mode where each block of plaintext is encrypted independently with the same key. Identical plaintext blocks produce identical ciphertext blocks.
Advantages
- Simple to implement and understand
- Supports parallel encryption/decryption
- No error propagation between blocks
Disadvantages
- Reveals patterns in plaintext (highly insecure)
- Vulnerable to replay attacks
- Not suitable for encrypting large amounts of data
- Does not provide strong confidentiality
Technical Details
Formula: Ci = EK(Pi)
Where: Ci = ciphertext block, EK = encryption function with key K, Pi = plaintext block
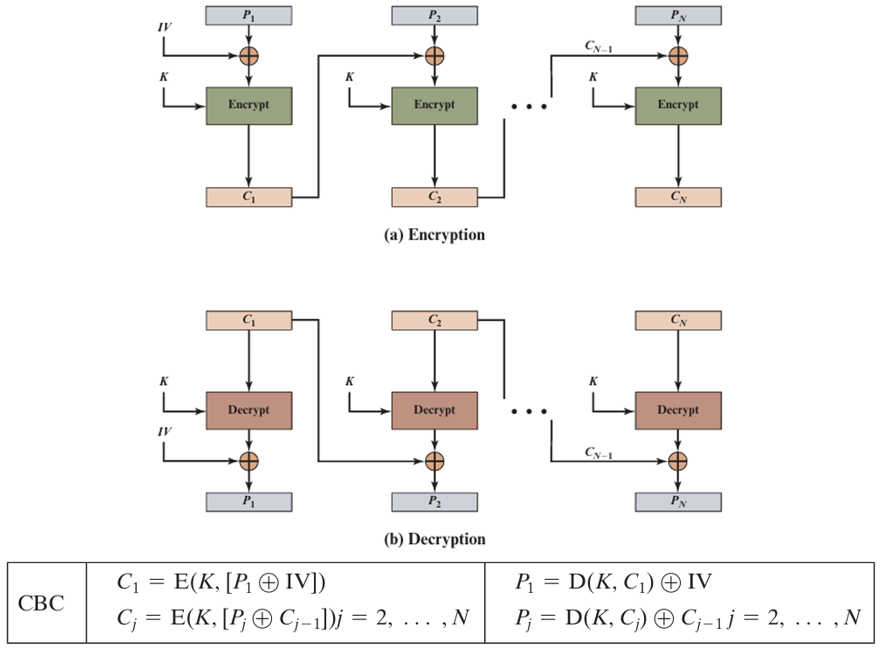
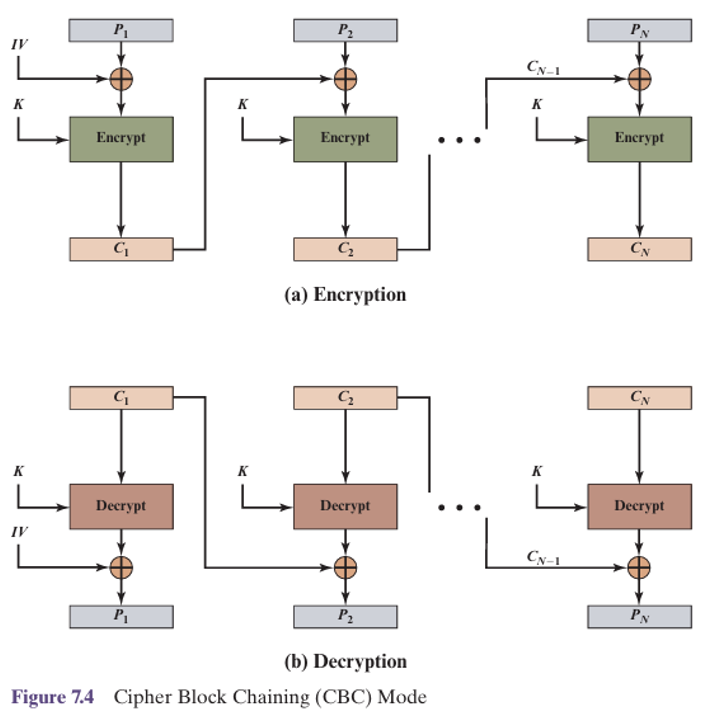
Cipher Block Chaining (CBC) Mode
Cipher Block Chaining (CBC) Mode
Each plaintext block is XORed with the previous ciphertext block before being encrypted. This creates a dependency chain between blocks, hiding patterns.
Advantages
- Hides patterns in plaintext
- Better security than ECB for long messages
- Widely used and well-studied
Disadvantages
- Encryption is sequential (cannot be parallelized)
- Errors in ciphertext propagate
- Requires an Initialization Vector (IV)
- Requires padding for the last block
Technical Details
Formula: Ci = EK(Pi ⊕ Ci-1), with C0 = IV
Where: IV = initialization vector, ⊕ = XOR operation
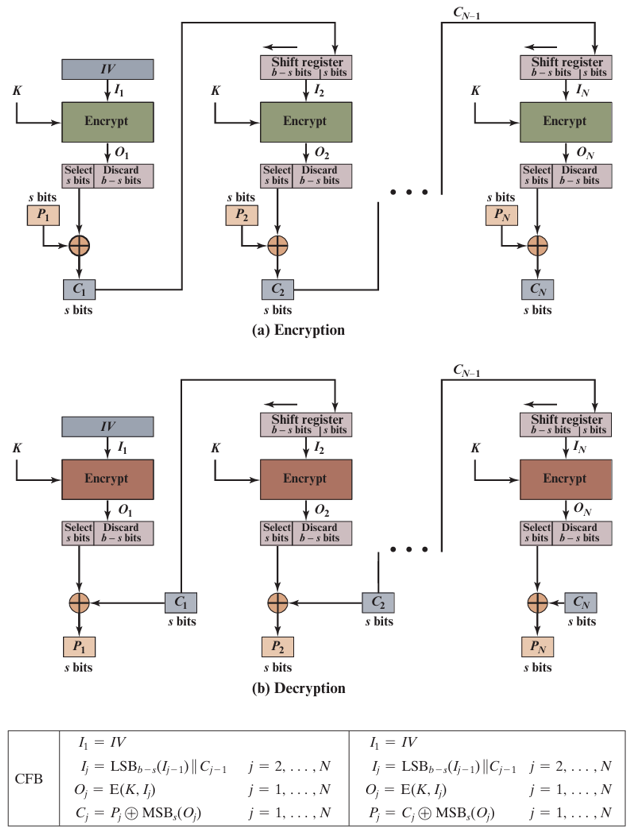
Cipher Feedback (CFB) Mode
Cipher Feedback (CFB) Mode
Turns a block cipher into a self-synchronizing stream cipher. The previous ciphertext block is encrypted and then XORed with the plaintext to produce the next ciphertext block.
Advantages
- Can operate on smaller units than the block size
- Self-synchronizing after errors
- Only the encryption function of the cipher is needed
Disadvantages
- Encryption is sequential
- Errors propagate for several blocks
- Slower than other modes due to feedback
Technical Details
Formula: Ci = Pi ⊕ EK(Ci-1), with C0 = IV
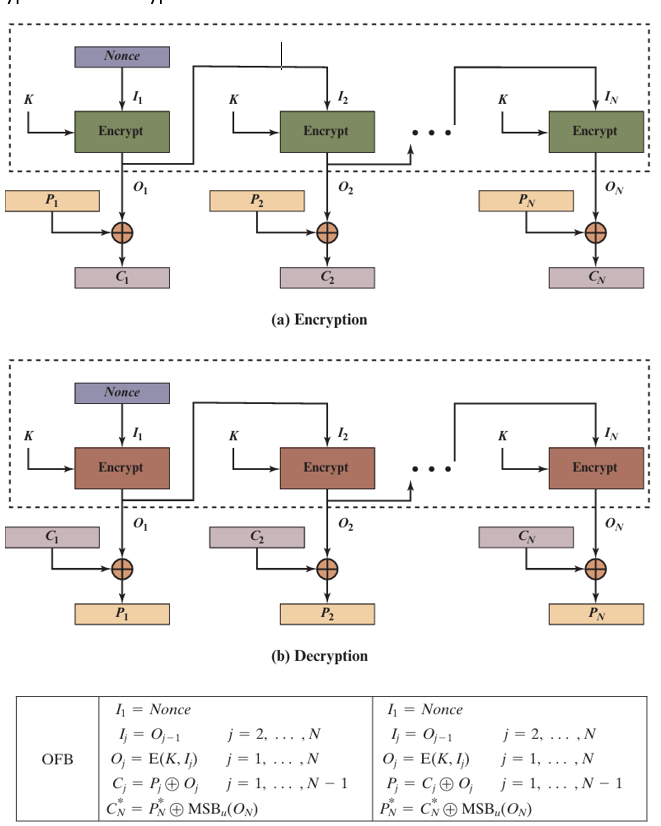
Output Feedback (OFB) Mode
Output Feedback (OFB) Mode
Turns a block cipher into a synchronous stream cipher. It generates a keystream by repeatedly encrypting an IV, which is then XORed with the plaintext.
Advantages
- Bit errors in ciphertext do not propagate
- Keystream can be pre-computed
- Only encryption function is needed
Disadvantages
- Vulnerable to stream reuse attacks if IV is repeated
- Not self-synchronizing
- Encryption is sequential
Technical Details
Keystream: Oi = EK(Oi-1), with O0 = IV
Encryption: Ci = Pi ⊕ Oi
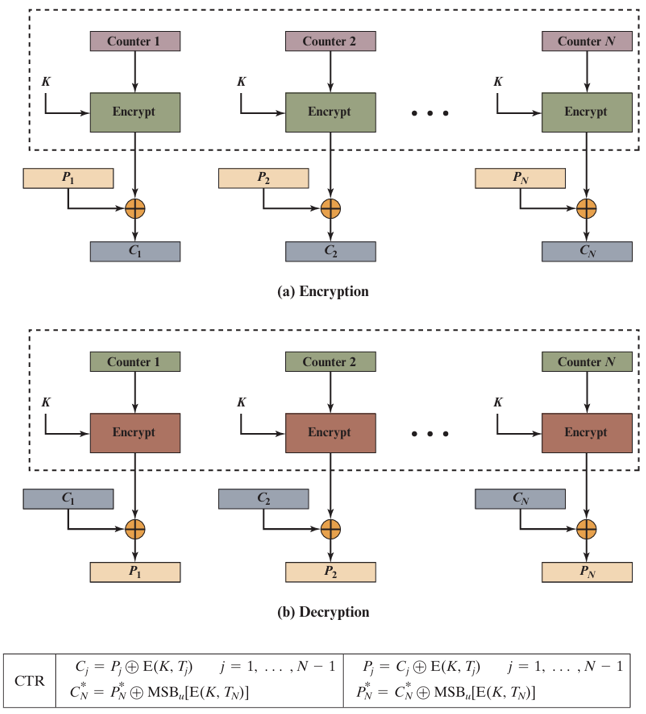
Counter (CTR) Mode
Counter (CTR) Mode
Also turns a block cipher into a stream cipher. It generates a keystream by encrypting successive values of a "counter". This mode is highly parallelizable.
Advantages
- Highly parallelizable for high performance
- Random access to any block is possible
- No padding required
- Keystream can be pre-computed
Disadvantages
- Requires a unique counter for every block (nonce)
- Catastrophic failure if counter/nonce is reused
- No built-in integrity protection
Technical Details
Keystream: Oi = EK(Nonce || Counteri)
Encryption: Ci = Pi ⊕ Oi
Review Questions
Question 1: ECB vs CBC Security
Why is ECB mode considered insecure for encrypting large amounts of data or structured data, while CBC mode provides better security?
Answer
ECB mode encrypts identical plaintext blocks into identical ciphertext blocks, revealing patterns in the data. This is particularly problematic for structured data like images or documents where patterns are common. CBC mode XORs each plaintext block with the previous ciphertext block before encryption, ensuring that identical plaintext blocks produce different ciphertext blocks, thus hiding patterns and providing better confidentiality.
Question 2: CFB vs OFB Error Handling
Compare how CFB and OFB modes handle transmission errors. Why does OFB have an advantage in noisy communication channels?
Answer
In CFB mode, errors propagate because the decryption of each block depends on previous ciphertext blocks. A single bit error in ciphertext will cause errors in the current block and potentially the next few blocks (depending on the feedback size). In OFB mode, the keystream is generated independently of the ciphertext. A transmission error affects only the specific bit where it occurred, without propagating to other blocks. This makes OFB more suitable for noisy channels where bit errors are likely.
Question 3: CTR Mode Advantages
What are the main advantages of CTR mode over CBC mode? Explain in terms of implementation benefits in software, hardware, and decryption throughput.
Answer
CTR mode offers several advantages over CBC:
- Parallel Processing: Both encryption and decryption can be parallelized since blocks don't depend on previous results.
- Throughput: Higher decryption throughput possible with multiple processors.
- Implementation: Requires only the encryption function, simplifying hardware/software design.
- Precomputation: Keystream can be generated before data is available.
- Random Access: Allows decryption of any block without processing previous blocks.